IDOR Vulnerability Grants Unauthorized Access to Paid eBooks at IGI Global

Introduction
In May 2022, I identified a critical security vulnerability on IGI Global's website www.igi-global.com that provides access to free and paid books as well as academic journals. In detail, I noticed that the web application is susceptible to an Insecure Direct Object References (IDOR) vulnerability. This vulnerability allows any unauthenticated attacker from the Internet to gain free access to paid eBook contents.
Despite numerous attempts at contacting IGI Global for responsibly disclosing the issue in a coordinated manner, all my inquiries were ignored. Therefore, this vulnerability was publicly disclosed after 90 days.
A social media account named IGI Global Admin reached out via LinkedIn on 12th September 2022, three days after public disclosure:
"Thank you for bringing this to our attention. Unfortunately, we could not find any direct communications pertaining to this issue. We take these types of issues seriously and once it was brought to our attention, this issue was remedied within less than an hour."
IGI Global (formerly Idea Group Inc.) is a U.S.-based international academic publishing company headquartered in Hershey, Pennsylvania that publishes books and academic journals across 11 subject areas including: Business and Management; Computer Science and Information Technology; Education; Engineering; Environment and Agriculture; Government and Law; Library and Information Science; Media and Communications; Medicine and Healthcare; Security and Forensics; and Social Sciences and Humanities.
In 2019, IGI Global was assessed in a Springer Nature white paper as the 7th largest scientific, medical, and technical (STM) publisher in a top ten list of publishers, with a total of 116 books, 2,286 chapters, 2,339 citations, and an average of 20 citations per book. IGI Global and its activities are covered in multiple professional publications.
- Source: https://en.everybodywiki.com/IGI_Global
What is IDOR?
Insecure direct object references (IDOR) is a type of access control vulnerability that arises when an application uses user-supplied input to access objects directly. Without proper access controls or other protection measures, attackers can manipulate these references to gain unauthorized access to data.
As an example, an application may use simple numeric object references such as https://example.com/edit_profile.php?id=10 within GET and POST requests to edit a user's profile. An attacker can easily exchange or iterate such identifiers like the id parameter and try to gain unauthorized access to other objects. If the application does not implement proper access controls in our example URL above, an attacker will be able to access and edit other user profiles without authorization by just guessing another valid profile id like 11, 12 or 200.
Many times developers use unique identifiers like UUIDs to prevent attackers from guessing valid object references. However, implementing proper access controls is far more important than using UUIDs, since UUIDs may also be leaked in error messages, stack traces or application logs.
Exploitation
In May 2022 I identified that IGI Global’s online bookstore is susceptible to IDOR. An unauthenticated attacker from the Internet can exploit this issue to gain unauthorized full access to paid eBook contents without actually paying for the access.
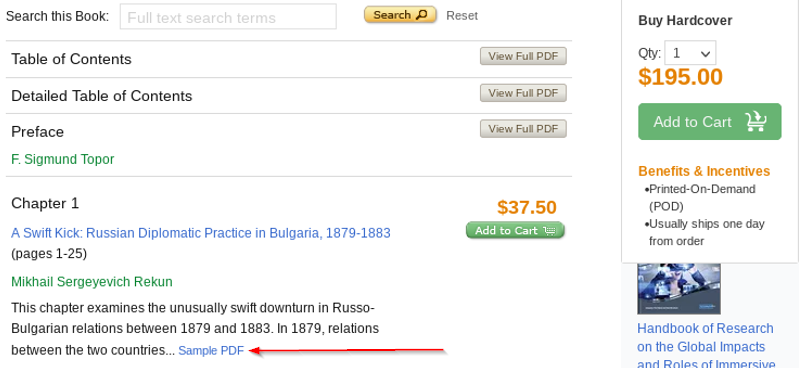
Usually, only a few pages of an eBook are available for free such as the Table of Contents or Preface. All other chapters of a paid eBook are accessible in full after a purchase only. However, sometimes a Sample PDF hyperlink exists, which provides a reading sample with limited content of a specific eBook chapter. Nonetheless, to read the entire chapter, either the eBook itself or the specific chapter has to be purchased.
Proof-of-Concept (PoC)
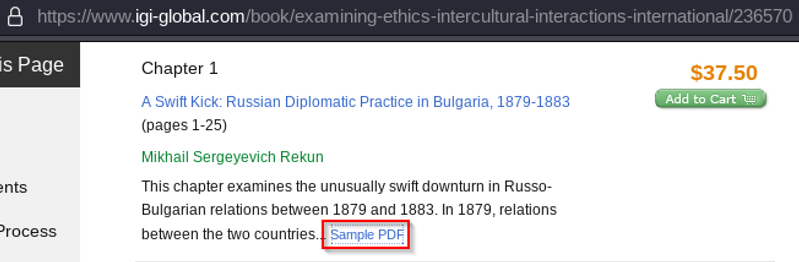
To exemplify the identified IDOR vulnerability, we will use a random paid eBook from the regular IGI Global online bookstore, such as:
- https://www.igi-global.com/book/examining-ethics-intercultural-interactions-international/236570
As previously mentioned, the bookstore will provide full access to a few eBook contents for free. For example, the Table of Contents can be accessed in full for free using the following URL:
- https://www.igi-global.com/pdf.aspx?tid=251110&ptid=236570&ctid=15&t=Table of Contents&isxn=9781799823773
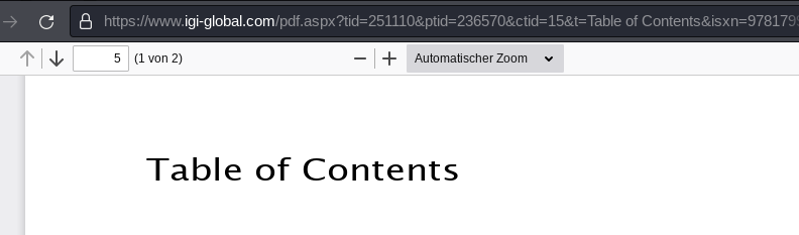
Hereby, the application URL contains several GET parameters like tid, ptid and ctid, which are used as references to a specific eBook, chapter etc. The Table of Contents PDF for example uses a tid parameter with a value of 251110 and is provided in full by the ASPX application endpoint pdf.aspx.
In comparison, the first chapter Chapter 1 of the aforementioned example eBook cannot be accessed in full for free. Only a reading sample is available by clicking on the Sample PDF hyperlink. Otherwise, it must be purchased.
The sample PDF is accessible at the following URL and is provided by a different ASPX application endpoint called viewtitlesample.aspx. Here, the Chapter 1 reading sample uses a different GET parameter called id with a value of 251113:
- https://www.igi-global.com/viewtitlesample.aspx?id=251113&ptid=236570&t=A Swift Kick: Russian Diplomatic Practice in Bulgaria, 1879-1883&isxn=9781799823773
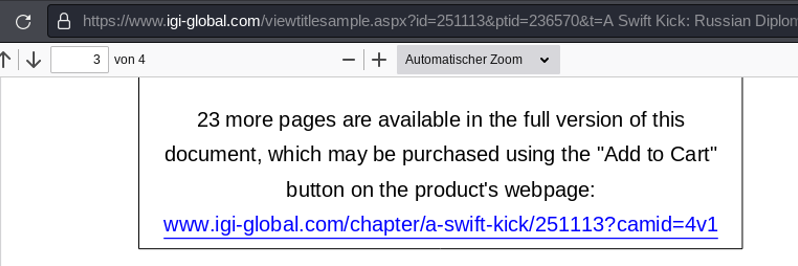
An attacker can now exploit an IDOR vulnerability by specifying the Chapter 1 object ID 251113 (GET parameter id) of the viewtitlesample.aspx endpoint at the pdf.aspx endpoint within the GET parameter tid. Basically replacing or iterating object IDs at the application endpoint pdf.aspx that usually grants full access to a few eBook chapters like ToC and Preface only. The other parameters such as ptid and ctid remain the same, as it is still the same eBook we are referencing to. Upon replacing the object ID, we obtain unauthorized full access to Chapter 1.
The following URL can be used by an unauthenticated attacker from the Internet to access the first chapter Chapter 1 of the aforementioned paid eBook for free, without purchasing the specific chapter ($37.50) or entire eBook ($195.00):
- https://www.igi-global.com/pdf.aspx?tid=251113&ptid=236570&ctid=15
Please note that the URL GET parameters t and isxn are optional and not required for successfully exploiting this IDOR vulnerability.
Proof of Concept (PoC) Video
Impact
An attacker exploiting this vulnerability gains unauthorized access to all paid eBook contents without actually purchasing the contents. This affects the confidentiality of data and can have an economic damage for IGI Global and affected authors, since the pay wall can be effectively bypassed.
Furthermore, successful exploitation may introduce legal disputes between IGI Global and publishers or authors.
Likelihood
The vulnerability can be abused by anyone on the Internet. No authentication or a user account is required to perform this attack. To discover this issue, an attacker needs to have moderate technical skills. However, replacing IDs or application endpoints in URL parameters is considered feasible by non-technical persons.
Exploitation of this vulnerability can be easily automated to retrieve an entire paid eBook, since chapter IDs are iterated and no UUIDs are used. An attacker can locate the numeric object ID of a beginning chapter (e.g., Table of Contents) and the ID of a closing chapter (e.g., About the Contributors) and iterate over this range to retrieve all eBook chapters as individual PDF files.
IGI Global’s online bookstore manages thousands of paid eBooks. Some of which are offered for a price of several thousands of dollars. Therefore, economic loss and the incentive for cyber criminals may be considered high.
Recommendation
I recommend following security best practices to prevent insecure object references by adhering to the following principles:
- Verify if users are authorized to access objects (proper access controls)
- Use object references or IDs that cannot be guessed, such as UUIDs
For more information on insecure object references, see:


CVSS Risk Rating
| Risk | HIGH |
| Base Score | 7.5 |
| Vector String | CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N |
Timeline
2022-05-27: Initial Contact via Email
I contacted IGI Global via email at [email protected].
Result: Automatic reply that a representative will respond to my email. However, no response so far.
2022-06-03: Contacting IGI Global via Twitter (Part I)
I tweeted about my vulnerability identification and referenced IGI Global's Twitter handle @igiglobal.
Result: No response so far.
2022-06-11: Contacting the Vice President Of Technology
I contacted the Vice President of Technology at IGI Global, Justin North, directly via email at [email protected].
Result: No response so far.
2022-06-18: Contacting IGI Global via Twitter (Part II)
I tweeted about my vulnerability identification and referenced IGI Global's Twitter handle @igiglobal a second time.
Result: No response so far.
2022-06-22: Contacting Individuals via LinkedIn
I purchased LinkedIn premium to be able to contact various individuals working at IGI Global. Here, I contacted Justin North (Vice President of Technology) and Donald Haag (IT Manager), both working at IGI Global.
Result: No response so far.
2022-06-25: Contacting [email protected]
I contacted IGI Global via their resume email address at [email protected]. I asked for a contact person at IGI Global's IT department and outlined the criticality of my request.
Result: No response so far.
2022-06-29: Public LinkedIn Post
I published a LinkedIn post referencing IGI Global's user handle as well as the previously contacted employees Justin North and Donald Haag.
Later on, I additionally linked two IGI Global employees as well as Lindsay Wertman - the current president of IGI Global - in the comments section.
Result: No response so far.
2022-09-09: Public Disclosure
Due to the lack of feedback from IGI Global, the vulnerability was publicly disclosed after a waiting time of more than 90 days. I gave IGI Global multiple chances to respond to my contact attempts. However, not a single feedback was received.
Result: Unfixed vulnerability publicly disclosed on the Internet.
2022-09-12: Response from IGI Global Admin on LinkedIn
"Thank you for bringing this to our attention. Unfortunately, we could not find any direct communications pertaining to this issue. We take these types of issues seriously and once it was brought to our attention, this issue was remedied within less than an hour." - IGI Global Admin
Result: Vulnerability finally addressed - three days after public disclosure.
With the help of public pressure, vulnerabilities are then often addressed and fixed in a timely manner. As seen.



Member discussion