Jailbreaking iPhones has been a constant tug-of-war between users seeking freedom and Apple tightening its grip. Early on, jailbreakers enjoyed full-root access to the iOS operating system that even remained persistent during reboots. A so called untethered, rootful jailbreak. Some of them even being executable from a Safari web browser instantly. Crazy times!
However, Apple quickly responded with beefed-up security measures, making it harder and harder to compromise the iOS ecosystem. Despite Apple's efforts, the jailbreaking community persisted, finding new ways to break the iOS system and introduced security measures. Over time though, Apple's security measures became more sophisticated, leading to the emergence of rootless jailbreaks over rootful ones.
Terminology
In the world of jailbreaking, many terminologies exist. From thethered to unthethered jailbreaks or rootless and rootful ones. What those mean, will be clarified in the following.
Untethered vs. Tethered vs. Semi
In a tethered jailbreak, the device needs to be connected to a computer each time it is restarted or turned off in order to fully boot up. Without this connection, the device remains in a semi-functional state and may not even boot up properly.
An untethered jailbreak is more user-friendly. Once the device has been successfully jailbroken, it can be restarted or turned off without the need for a computer. The device will fully boot up and retain its jailbroken state without any external assistance. Untethered jailbreaks are generally preferred by users as they offer more freedom and flexibility. However, they are quite rare in the modern days.
A semi-tethered jailbreak is a compromise between tethered and untethered jailbreaks. The device can function normally without any external assistance after a restart, but most jailbreak features are disabled. To re-enable the full set of jailbreak features, the device needs to be connected to a computer and the jailbreak process has to be repeated. This allows users to have a more stable device operation after a restart but still requires some intervention to access all jailbreak functionalities.
Finally, there are semi-untethered jailbreaks. The device can function normally without any external assistance after a restart. The full set of jailbreak features are either automatically enabled after boot or require a re-jailbreaking via a mobile app previously installed. No external assistance or computer connection required.
Rootful vs. Rootless
Rootful jailbreaks grant full control over the iOS file system. They consist of a chain of vulnerabilities, actively and successfully exploited, to obtain privileged access to an iOS operating system. In the end, if the attack succeeds, the iOS operating system is successfully compromised - unlocking access to the privileged root user acccount as well as the root (/) file system.
Rootless jailbreaks on the other hand are not able to achieve such full-access privilege escalation. Although one will still obtain access to the privileged root user account, access to the iOS root filesystem (also known as rootfs or the system partition) is denied. Rootless jailbreaks will not attempt to exploit and bypass relevant security measures introduced by Apple that actively hinder tampering with this important OS area - such as Signed System Volume (SSV). If tweaks and tools are required that need such access to the root filesystem, a rootless jailbreak would not be a viable solution.
How to Jailbreak?
For this blog post, I will not go into detail on how to jailbreak an iDevice nor which Jailbreak methods exist. Please conduct some research yourself.
Jailbreak button within the app.Here some links to point you into the right direction:



Why Rootless?
With iOS and iPadOS 15 Apple unleashed its Signed System Volume (SSV) security mitigation feature on the mobile platform for the first time. This feature first debuted on macOS as a means of verifying the integrity of system content at runtime with the help of a kernel mechanism. It basically rejects everything that lacks a valid cryptographic signature, which is verified by the SSV feature.
This ensures that only signed code and files are executed during the runtime of the iOS Operating System. Basically the reason why rootless jailbreaks cannot provide access to the privileged root (/) filesystem.
Bypassing such a cryptographic security feature requires a lot of work and complex chains of vulnerabilities. Furthermore, even if such attack succeeds, it likely renders the iOS Operating System a bit more unstable than usual, which is an undesired side effect of exploitation.
Due to this, many jailbreaks nowadays offer a rootless exploitation of iOS instead. Still providing access to the highly privileged root user account and most of the important iOS system paths but as said, no access to or tampering with the root (/) filesystem. This is sufficient for most jailbreakers that just want to install some tweaks and themes onto their iDevices. Such tweaks and toolings are installed in /var/jb and bypass the need for privileged root (/) filesystem access (read more here). Due to this, a rootless jailbreak can easily be hidden or removed on the fly. Furthermore, it is less likely to be detected by root detection mechanisms.
Pentesting Requirements
Penetration testers are often tasked to audit the security level of mobile applications. To perform such tasks, various tests must be conducted that require some form of privileged access to the Operating System.
Common Security Tests
Some of the conducted security testing in general are the following:
- Analyzing the data storage of application data
- Requires access to the iOS filesystem to inspect application data stored
- Intercepting the iOS application traffic from the iDevice to a remote application server (API backend)
- Requires access to the iOS filesystem to install 3rd party packages that are able to disable SSL certificate validations and pinning (e.g. SSL Kill Switch 3)
- Analyzing the data stored into the iOS key chain by the mobile app
- Requires access to the iOS filesystem to install 3rd party packages that are able to inspect the iOS KeyChain (e.g. Python3 and Objection)
- Hooking into the mobile app's runtime for analysis and tampering
- Requires access to the iOS filesystem to install 3rd party packages that are able to hook an iOS mobile app (e.g. Python3, Frida and Objection)
Are Rootless Jailbreaks Sufficient?
From the aforementioned security tests conducted by a penetration tester, one may assume that a rootful jailbreak is required.
Let's dive into the world of rootless jailbreaks and validate, whether all pentesting test cases can be conducted without access to a rootful jailbreak and the privileged root (/) filesystem of iOS.
Analyzing Local Data Storage
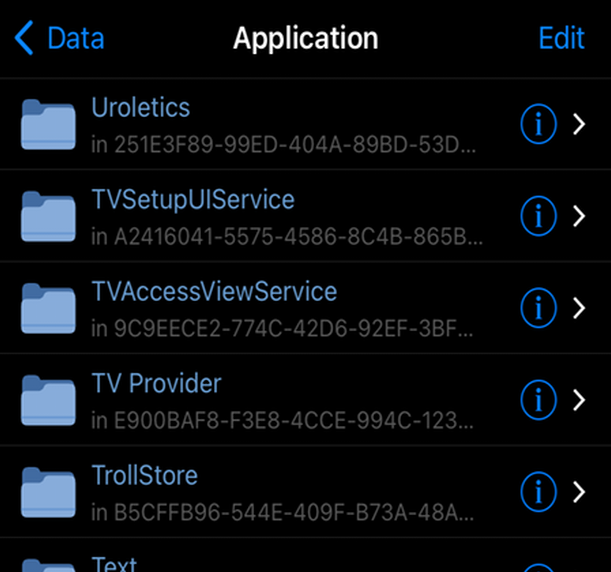
Analyzing the data storage of iOS mobile applications requires access to the iOS filesystem. Application data is typically installed at /var/mobile/ and should therefore not require any privileged access to the root (/) filesystem path, which is only granted by a rootful jailbreak.
So let's head over to our rootless jailbroken iDevice, open up the Sileo package manager and install the Filza File Manager tool. This tool installs as mobile application onto our iDevice and grants visual access to the iOS filesystem.
As can be seen from the next screenshots, a rootless JB is sufficient to gain access to the underlying iOS filesystem. We can use Filza to inspect any application's storage path for insecure data storage (databases, logs, secrets etc.).

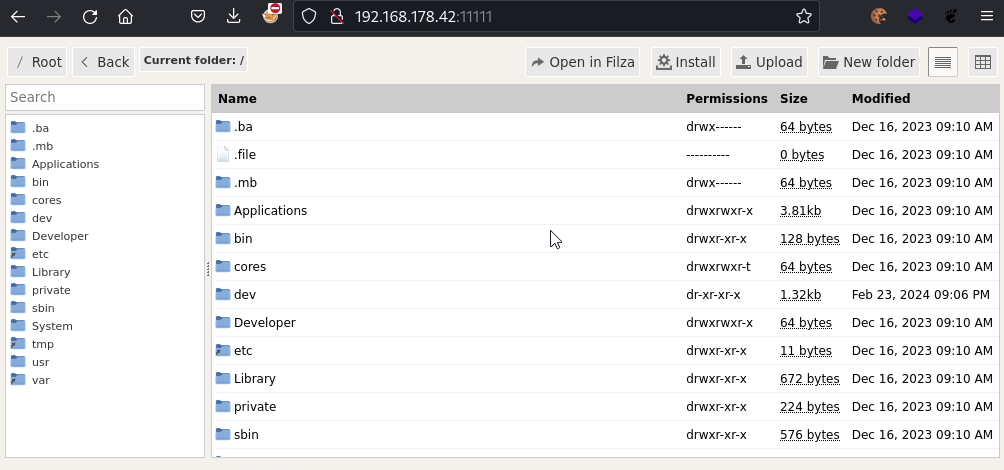
Alternatively, a rootless JB also provides access to the filesystem via OpenSSH.
However, the OpenSSH binary as well as many other OS related binaries such as cd, ls, rm etc. may not have the necessary entitlements to operate on the iOS app data path /var/mobile/Containers/Data/. You may receive permission errors like Operation not permitted and cannot open directory. This depends on the Jailbreak used and the installed package versions from Sileo.
If you still want to patch the entitlements of specific binaries manually, you can use the
ent-cman script developed by blanxd. The latest script is available at https://blanxd.is-a-geek.com/tmp/2024-03-25/.Another cool option to bypass such limitations, in case you still receive permission errors, is by mounting Filza's WebDAV server directly. As Filza itself has the necessary entitlements to operate on the data directory, mounting the WebDAV server will work flawlessly without permission errors.
# install davfs2 package
wget http://ftp.de.debian.org/debian/pool/main/d/davfs2/davfs2_1.6.0-1_amd64.deb
sudo dpkg -i davfs2_1.6.0-1_amd64.deb
# create a mount dir
sudo mkdir -p /mnt/iphone-app-data
# mount filza's webdav server
sudo mount -t davfs http://<FILZA-IP>:11111/var/mobile/Containers/Data/Application/ /mnt/iphone-app-dataMounting Filza's WebDAV server
Afterwards, our target iOS application data will be available natively at /mnt/iphone-app-data/. Combine with git and diff to detect and analyze data changes during app usage.
Intercepting SSL/TLS Network Traffic
Intercepting the network traffic of an iOS application typically requires installing a 3rd party certificate onto the iDevice. This does not require a rootful jailbreak and can be done on a regular, non-jailbroken iDevice.
Just configure your intercepting proxy of your choice, grab the SSL certificate of it and put it onto your iDevice. I personally use PortSwigger's BurpSuite intercepting proxy.

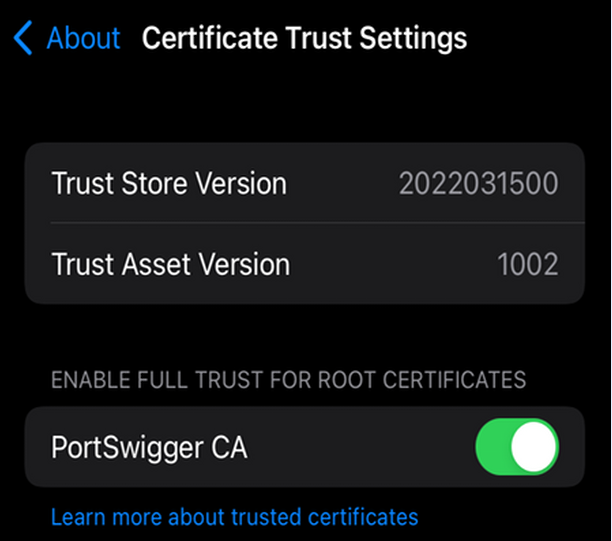
Upon installing and trusting the intercepting proxy's SSL certificate globally, we can successfully intercept SSL/TLS network traffic within mobile applications.
However, there is one key aspect left. What about SSL pinning? How can we as penetration tester disable SSL certificate validation if a mobile app strictly implements this?
You can install this package from the alias20 repository, which you have to manually add into Sileo first.
Repo source: https://alias20.gitlab.io/apt/
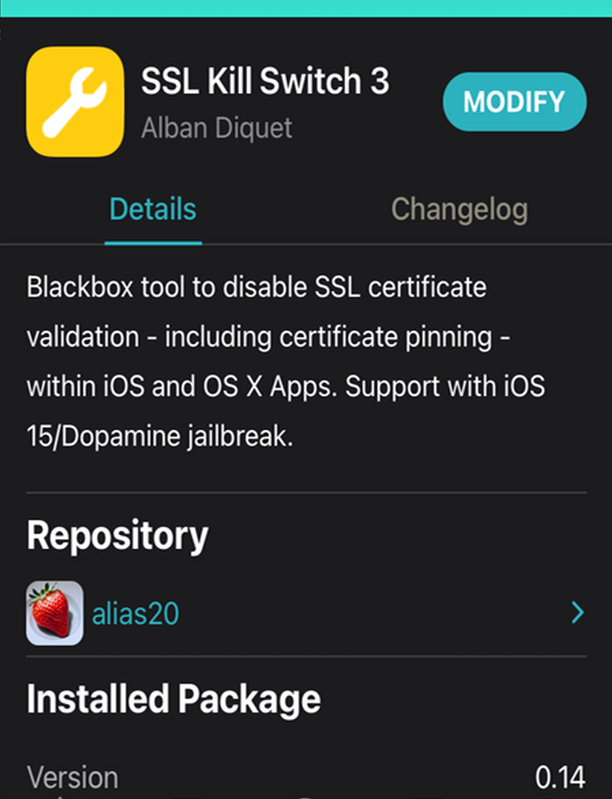
Afterwards, a new settings entry will be available that allows one to enable the SSL Kill Switch 3 tweak to disable all SSL certificate validations.
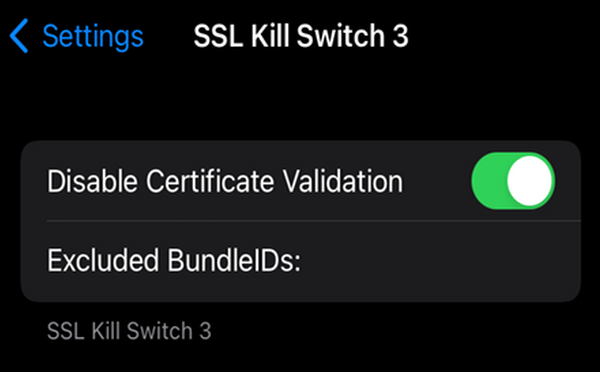
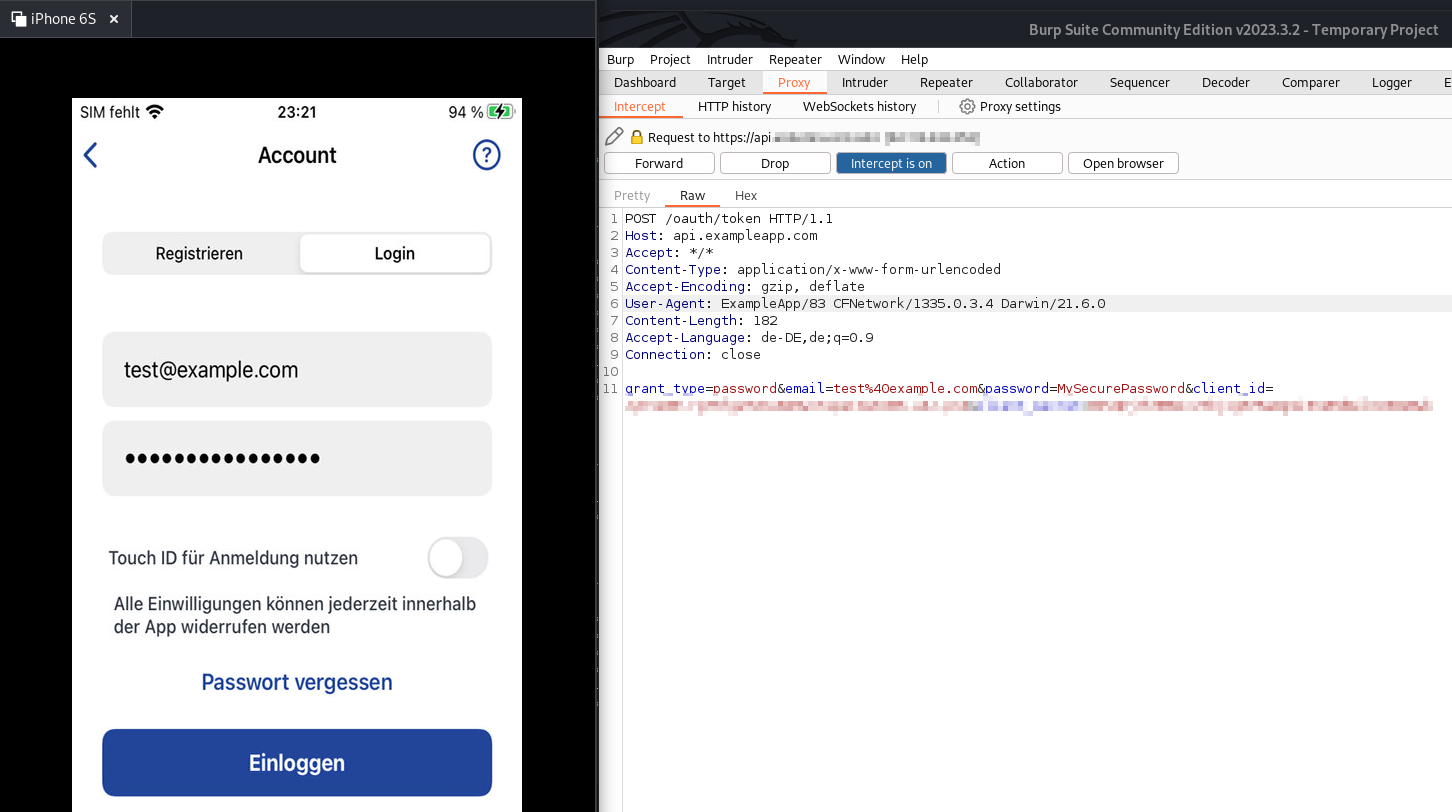
Hooking iOS Apps and Inspecting the KeyChain
Last but not least, it should be possible to hook iOS apps and inspect the iOS KeyChain for proper storage of sensitive application data.
In order to fullfill these tasks, we can install Python3 onto our iDevice using Sileo. More importantly though, we will install frida.
Afterwards, we have to connect to our iDevice via SSH and start the Frida server with root privileges (here using sudo instead of the root user directly).
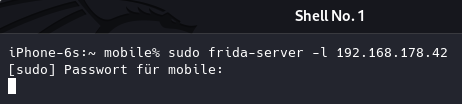
Afterwards, the frida server will be up and running on the iDevice. As we have defined the server to listen on our local Wifi IP address of our iDevice, we can connect from any other machine within the local LAN using a frida client.
The frida client can be installed the following way:
# create virtual environment
virtualenv venv
source venv/bin/activate
# install frida and objection for hooking
pip install frida
pip install objectionAfterwards, we can issue the following commands:
# list app processes
frida-ps -ai --host <IP-OF-IDEVICE-WHERE-FRIDA-SERVER-RUNS>
# hook an iOS application process
objection -N -h <IP-OF-IDEVICE-WHERE-FRIDA-SERVER-RUNS> -g <IDENTIFIER-OF-IOS-APP-OR-PID>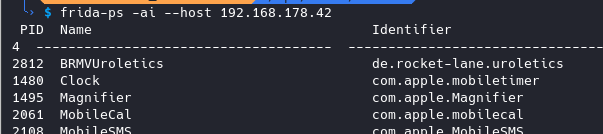
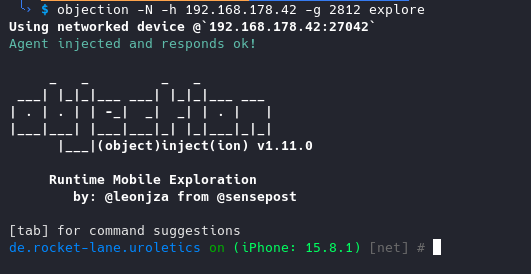
Once objection hooked the iOS app, we can issue one of the following commands:
# obtain some binary infos about the app
ios info binary
# dump the iOS key chain
ios keychain dump
# list the app's bundled files
ls
# inspect an app's bundle file
file cat <filename.extension>
# dump iOS shared credentials cache
ios nsurlcredentialstorage dump
# inspect NSUserDefaults class
ios nsuserdefaults get
# dump stored cookies
ios cookies getcmdlets for objection
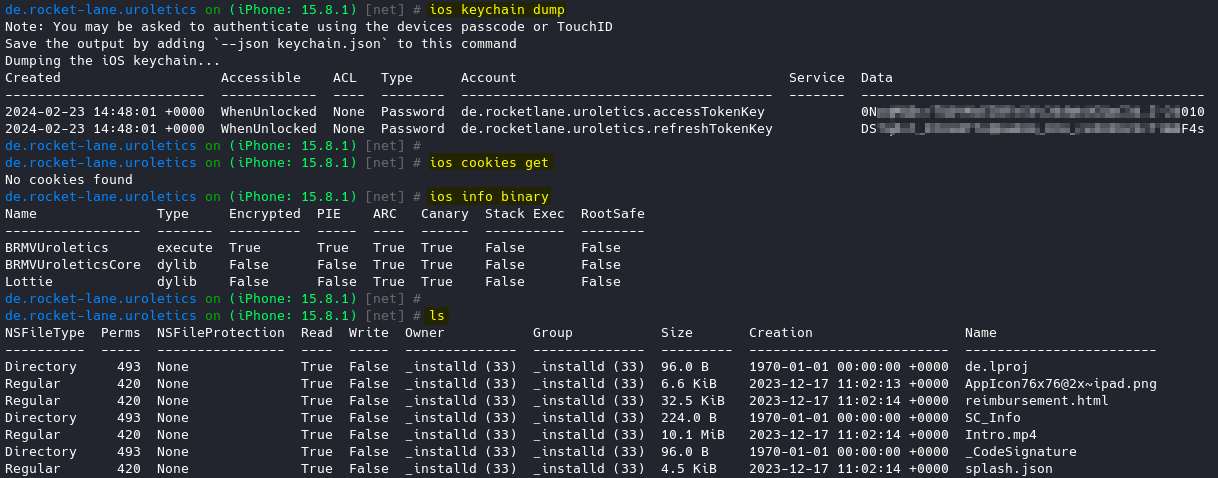
Installing Additional Tools
Finally, we may want to install further tools.
VNC Screen Sharing
For example to conveniently access the iDevice's screen from remote. Using a rootless jailbreak already provides us with SSH access. However, what about a VNC session?
- Open Sileo
- Add alias20 repo from above (if not yet done)
- Install screendump
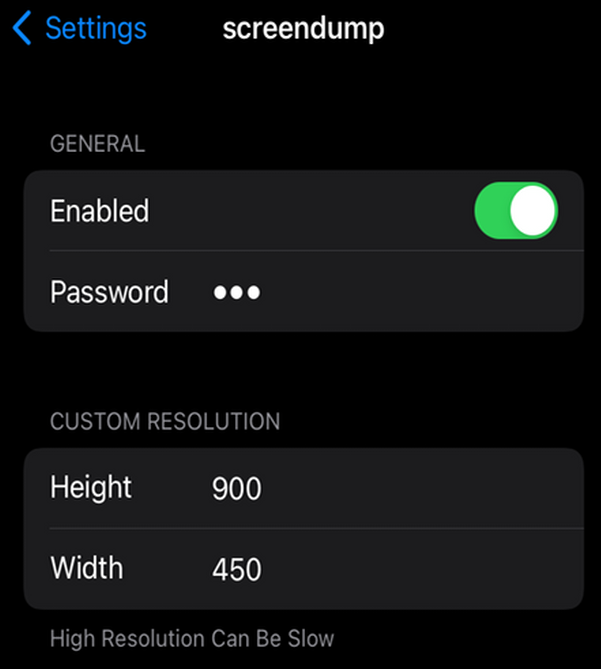
- Enable screendump in the iDevice's settings area
- Ensure to set a custom resolution, as this fixes connection issues.
Afterwards, we can use any VNC client to our liking in order to connect. I personally love Remmina, which is a RDP/VNC client for Linux. Just go ahead and connect to your iDevice's IP address on the TCP port 5900.

TrollStore
In order to install third-party iOS apps and sign them, we can make use of TrollStore.
- Open Sileo
- Search for TrollStore Helper
- Install the TrollStore Helper tweak
Afterwards, you will find a new mobile app on your iDevice. Using the TrollStore application, you can install and sign any .ipa apps you like.
You can even configure TrollStore to overwrite a default iOS app for persistence (e.g. the stocks app). Once you try to open the stocks app afterwards, TrollStore will open instead.
Resumée
As showcased, a rootless jailbreak is totally sufficient from the perspective of a penetration tester or mobile security auditor. There is no need for a rootful jailbreak, as most security tests can be conducted without requiring access to the iOS root (/) filesystem. This also holds true for most regular jailbreak enthusiasts.
We can happily:
- Access the iDevice via SSH as the user mobile;
- By using sudo we can easily escalate to root privileges
- Alternatively, we may authenticate directly as root
- Access the iDevice's local filesystem using the Filza File Manager from Sileo or native SSH
- Intercept SSL network traffic by installing a custom SSL certificate into the global trust store of the iDevice (no jailbreak required, works natively)
- Bypass SSL certificate validations and pinning using the SSL Kill Switch 3 tweak from Sileo
- Access the iOS KeyChain by hooking a mobile app via Frida and Objection
- Install and sign third-party apps like Dopamine for a semi-untethered jailbreak by using the TrollStore Helper tweak from Sileo that will install TrollStore
- Install various tweaks via Sileo repo manager and various repositories that just work. No errors, no crashes.
However, as most tweaks do not require access to the root (/) file system, which only a rootful jailbreak would provide, this is usually given. Nonetheless, you may observe that some of your wanted tweaks or tools are not yet adjusted to be fully supported on rootless jailbroken iDevices. There is also a slight chance that some tweaks and tools never will - especially those requiring access to the root (/) filesystem for a specific reason.
Cheers!















Discussion