Dynamically Granting Access to Selfhosted Services via TraefikShaper

TraefikShaper is a containerized Python Flask web application. It can programatically manipulate a Traefik IPAllowList middleware, which is typically used to whitelist IP addresses and grant access to proxy services behind a Traefik reverse proxy.
Hold on. Why would anyone do this?
The Use Cases
Let's imagine talking about selfhosting at your work or privately with a group of friends. The interest about the things you tell keep rising until one of your friends ask about showcasing a service or getting access to one for a few minutes. Now you find yourself in the struggle of granting access.
Most selfhosters keep their services on local lan and access it via a Virtual Private Network (VPN) from untrusted, remote networks. However, distributing VPN access to your home network to others, just for showcasing a proxy container or consuming a single services from time to time, seems intrusive and not a way to go.
What about your work place, where you cannot install a VPN client to access your beloved services running at home? Or one of your family members, asking for access to your local Emby/Plesk/Jellyfin instance to watch a single movie? Or your girlfriend, requiring access to your Stirling PDF instance during university class to adjust a single PDF file? Or people trying to access your pre-prod environment for testing and finding bugs?
These questions led to the development of TraefikShaper.
How it works
Upon successfully setting up TraefikShaper, granting access to one or more of your proxy services will look like this in a high-level summary:
- The remote party, currently not having access to a container service, queries your subdomain where the web service runs. A
403 Forbiddenerror message appears. Access is denied. - Then, the remote party can browse the
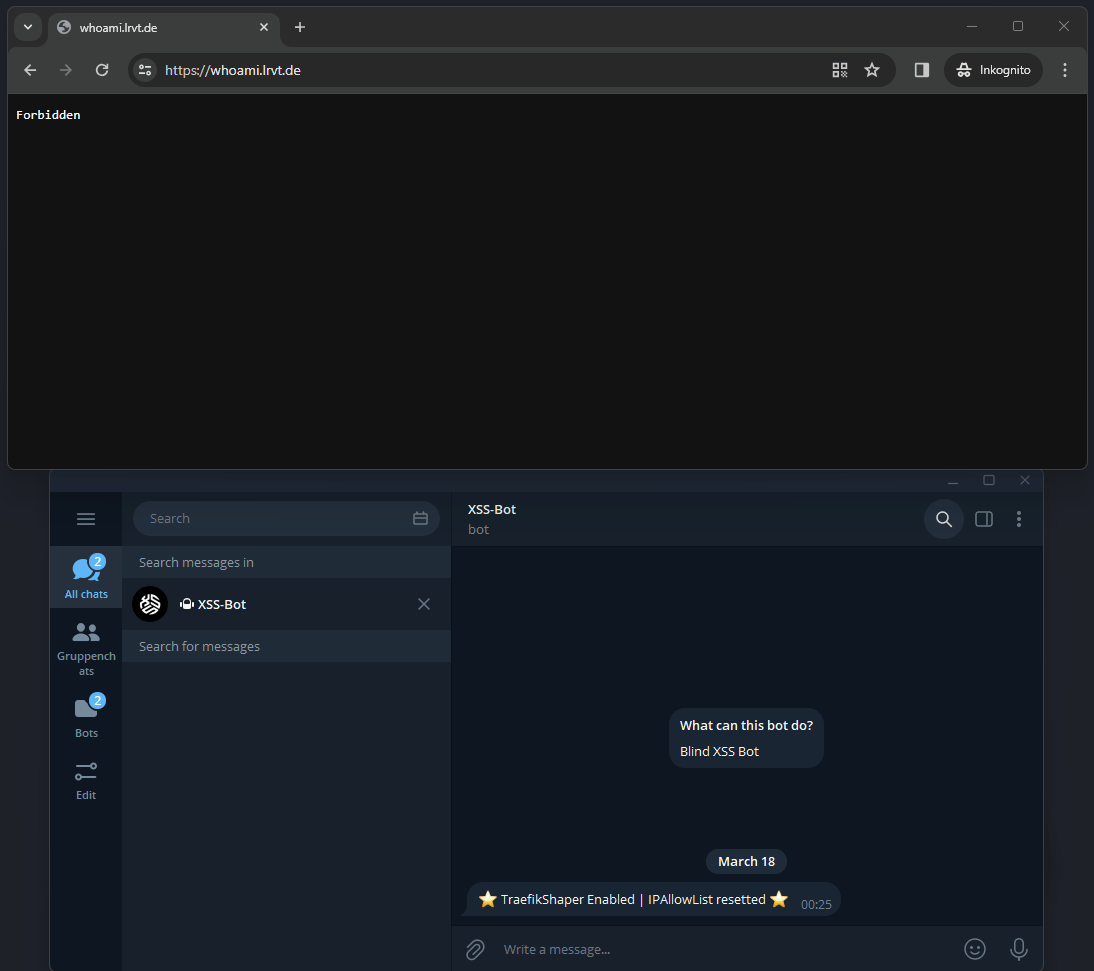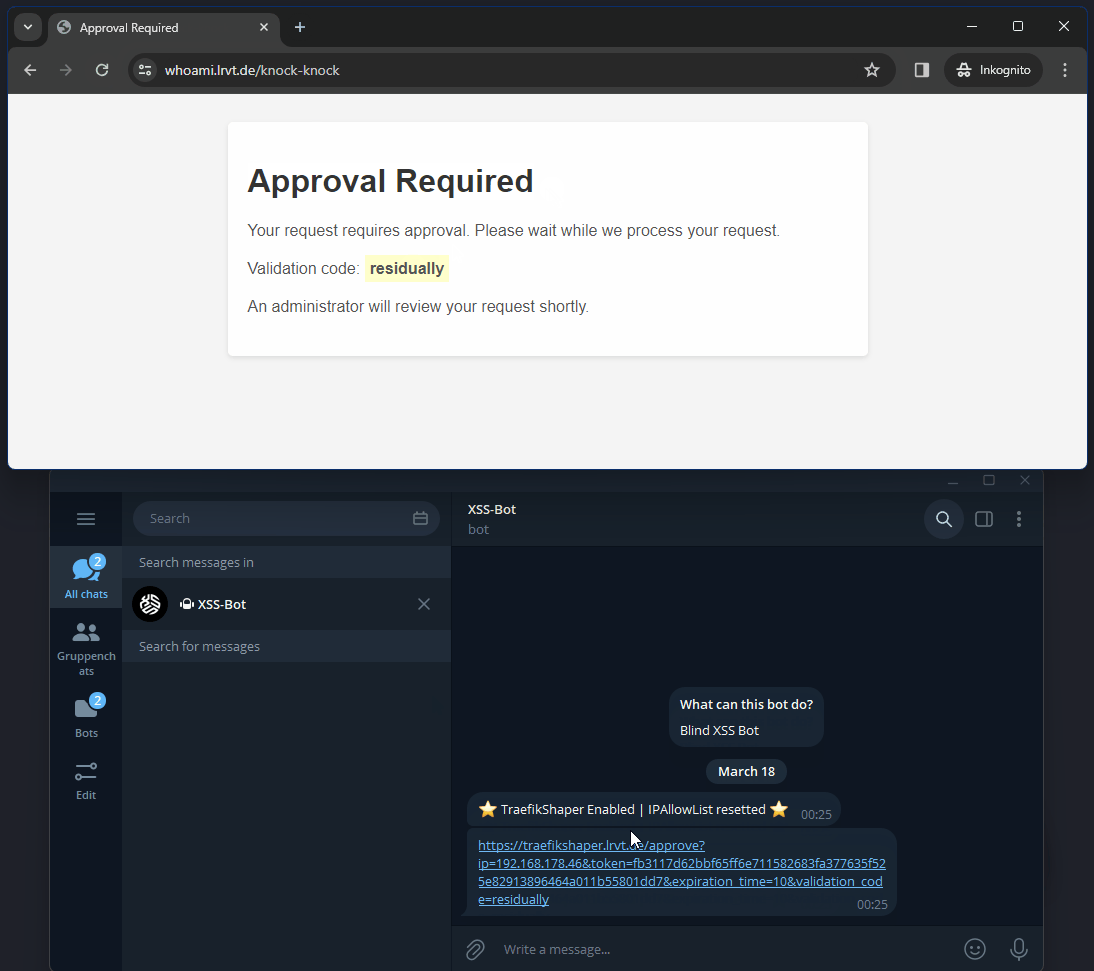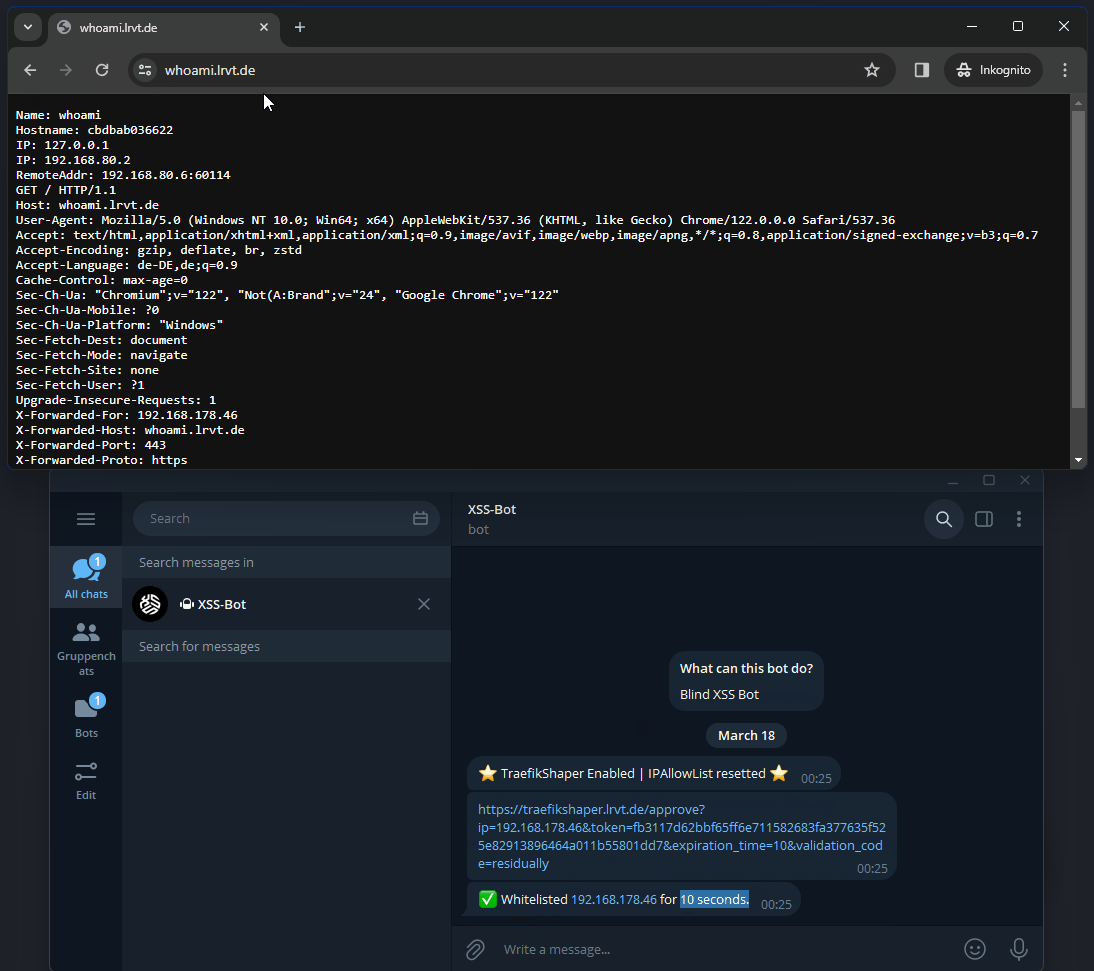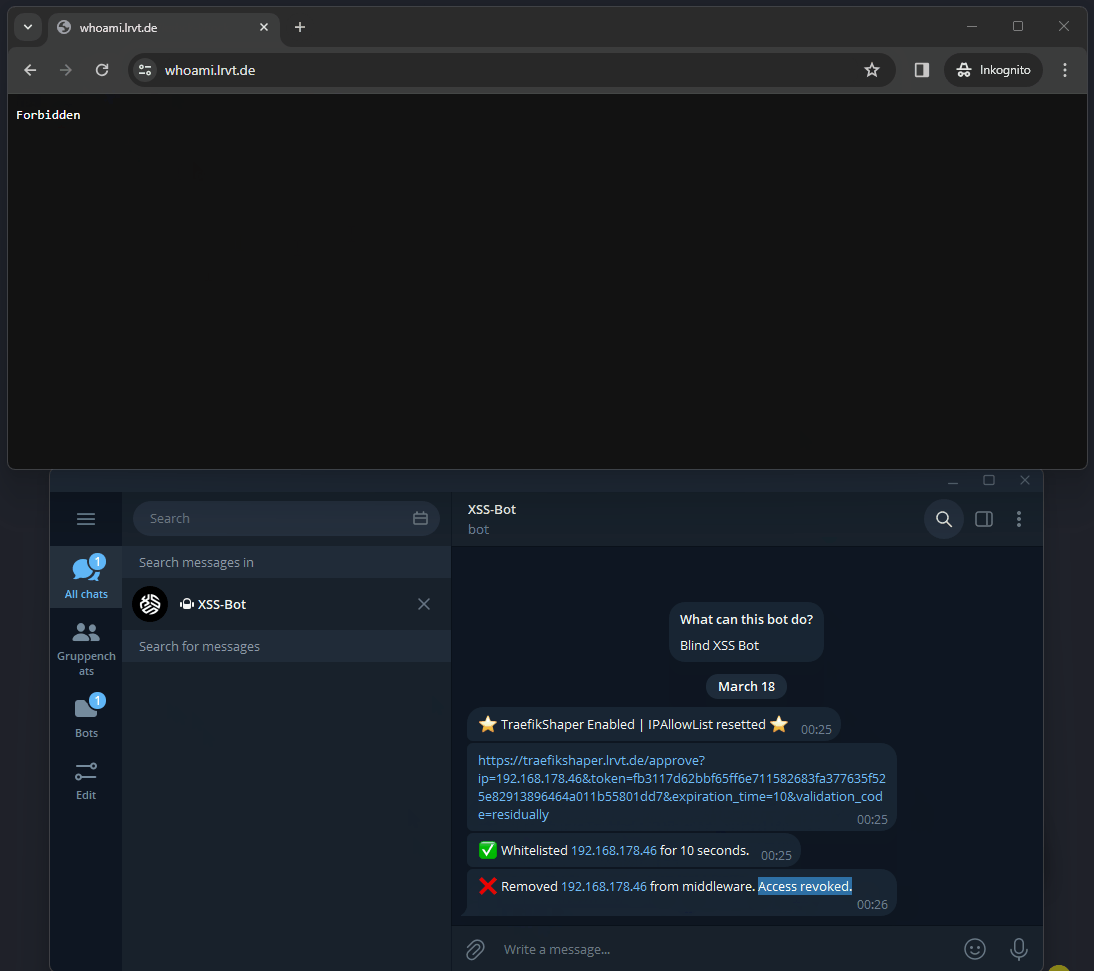
/knock-knockHTTP endpoint and receives a notification that an administrator was notified about granting you access to the web service. Furthermore, a random word as challenge is displayed. - Now, the admin receives an Apprise notification (e.g. via Telegram) with an approval link. The link contains the IP address of the external party as well as the same random word previously shown as challenge to the external party.
- The admin and external party may now compare the challenge word and if it matches, the admin can proceed opening the approval link. Once opened, the remote IP address of the external party is added to the IPAllowList middleware of Traefik. Access should now work, as the IP address is whitelisted and Traefik regularly monitors the dynamic configuration file for changes to apply them dynamically.
- The external party can now refresh the browser (F5) and gain access to the proxy service. The access time granted is limited though and expires within a pre-defined period by the administrator.
Resumee
Keen to try it out?
You can find the repository on GitHub:

Member discussion